Mastering Raspberry Pi Network Tunnel: A Comprehensive Guide
Network tunneling with Raspberry Pi has become an essential skill for tech enthusiasts, IT professionals, and hobbyists alike. As the Internet of Things (IoT) continues to grow, understanding how to create secure and efficient network tunnels using Raspberry Pi can significantly enhance your connectivity options. This guide will walk you through everything you need to know about Raspberry Pi network tunneling, from basic concepts to advanced configurations.
Whether you're setting up a remote access point, creating a secure connection between devices, or managing IoT networks, Raspberry Pi offers unparalleled flexibility and affordability. By leveraging its capabilities, you can achieve robust network solutions tailored to your specific needs.
In this article, we will explore the fundamentals of Raspberry Pi network tunneling, including step-by-step instructions, best practices, and expert tips. By the end of this guide, you'll have the knowledge and tools to implement secure and efficient network tunnels for your projects.
Read also:Mila Kunis Kissing Natalie Portman A Comprehensive Look At The Viral Moment
Table of Contents
- Introduction to Raspberry Pi Network Tunnel
- What is a Network Tunnel?
- Raspberry Pi Basics
- Setting Up Your Raspberry Pi
- Types of Network Tunnels
- Creating a VPN Tunnel with Raspberry Pi
- Securing Your Network Tunnel
- Troubleshooting Common Issues
- Advanced Techniques for Network Tunneling
- Conclusion and Next Steps
Introduction to Raspberry Pi Network Tunnel
Raspberry Pi network tunneling involves creating secure pathways for data transfer between devices over the internet. This technology is particularly useful for remote access, secure communication, and IoT device management. Understanding the basics of Raspberry Pi network tunneling can empower users to build custom solutions that meet their connectivity needs.
Why Use Raspberry Pi for Network Tunneling?
Raspberry Pi offers several advantages for network tunneling projects:
- Cost-effective hardware
- Flexible operating system options
- Strong community support
- Low power consumption
What is a Network Tunnel?
A network tunnel is a communication pathway that encapsulates data packets within another protocol to securely transfer information across networks. This technique is commonly used in virtual private networks (VPNs), remote desktop connections, and IoT device management.
Key Features of Network Tunnels
Network tunnels provide several critical features:
- Data encryption
- Authentication
- Compression
- Reliability
Raspberry Pi Basics
Raspberry Pi is a single-board computer designed for educational and hobbyist purposes. It has gained popularity due to its affordability, versatility, and ease of use. Raspberry Pi supports various operating systems, including Raspbian, Ubuntu, and others, making it suitable for a wide range of applications.
Popular Raspberry Pi Models
Some of the most popular Raspberry Pi models include:
Read also:Is Wil Wheaton Gay Exploring The Truth Behind The Rumors
- Raspberry Pi 4 Model B
- Raspberry Pi 3 Model B+
- Raspberry Pi Zero W
Setting Up Your Raspberry Pi
Before diving into network tunneling, you need to set up your Raspberry Pi properly. This involves installing an operating system, configuring network settings, and ensuring all necessary software is installed.
Step-by-Step Setup Guide
- Download and install Raspberry Pi OS.
- Connect your Raspberry Pi to a monitor, keyboard, and mouse.
- Power on your Raspberry Pi and complete the initial setup.
- Update the system using
sudo apt updateandsudo apt upgrade.
Types of Network Tunnels
There are several types of network tunnels, each suited for different purposes:
- IPsec
- OpenVPN
- SSH Tunneling
- GRE Tunneling
Choosing the Right Tunnel Type
Selecting the appropriate tunnel type depends on your specific requirements, such as security level, ease of setup, and compatibility with existing systems.
Creating a VPN Tunnel with Raspberry Pi
One of the most common applications of Raspberry Pi network tunneling is setting up a VPN. This allows users to access remote networks securely and privately.
Steps to Create a VPN Tunnel
- Install OpenVPN on your Raspberry Pi.
- Generate server and client certificates.
- Configure the OpenVPN server settings.
- Start the OpenVPN service and connect clients.
Securing Your Network Tunnel
Security is paramount when implementing network tunnels. Proper configuration and regular maintenance can help protect your data from unauthorized access and cyber threats.
Best Practices for Network Tunnel Security
- Use strong encryption protocols.
- Implement two-factor authentication.
- Regularly update software and firmware.
- Monitor network activity for suspicious behavior.
Troubleshooting Common Issues
Despite careful planning, issues may arise during network tunnel implementation. Understanding common problems and their solutions can save time and frustration.
Common Issues and Solutions
- Connection drops: Check network stability and restart services.
- Slow performance: Optimize tunnel settings and reduce data overhead.
- Authentication errors: Verify certificate configurations and user credentials.
Advanced Techniques for Network Tunneling
For experienced users, advanced techniques can enhance the functionality and security of Raspberry Pi network tunnels.
Exploring Advanced Features
- Load balancing for improved performance.
- Redundancy configurations for fault tolerance.
- Custom scripting for automation and monitoring.
Conclusion and Next Steps
Raspberry Pi network tunneling offers a powerful and flexible solution for secure and efficient data transfer. By following the guidelines and best practices outlined in this article, you can create robust network tunnels tailored to your specific needs.
We encourage you to experiment with different configurations and explore advanced features to further enhance your Raspberry Pi network tunneling projects. Don't forget to share your experiences and insights with the community by leaving comments or contributing to forums.
For more information on Raspberry Pi and network tunneling, refer to trusted resources such as the official Raspberry Pi documentation and reputable tech blogs. Happy tinkering!
References:
- Raspberry Pi Documentation: https://www.raspberrypi.com/documentation/
- OpenVPN Documentation: https://openvpn.net/community-resources/
- Network Security Best Practices: https://csrc.nist.gov/publications/detail/sp/800-46/final
The Iron Claw Budget: A Comprehensive Guide To Financial Mastery
Jonathan Turley Children: Exploring The Life, Expertise, And Legacy Of A Renowned Legal Scholar
Debbie Allen Bio: A Comprehensive Look At The Legendary Dancer, Actress, And Choreographer
PiTunnel Access your Raspberry Pi projects from anywhere
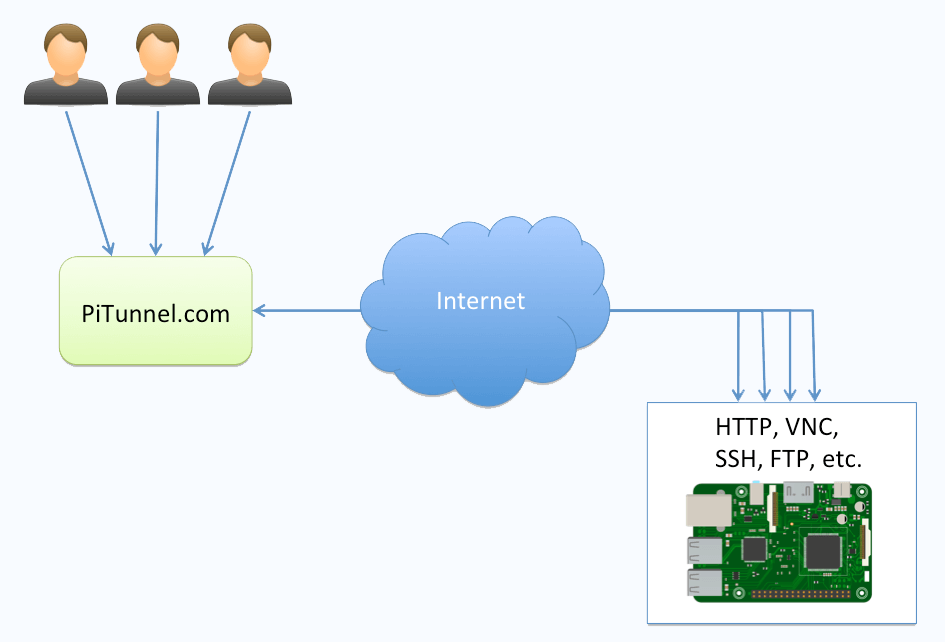
PiTunnel Access your Raspberry Pi projects from anywhere
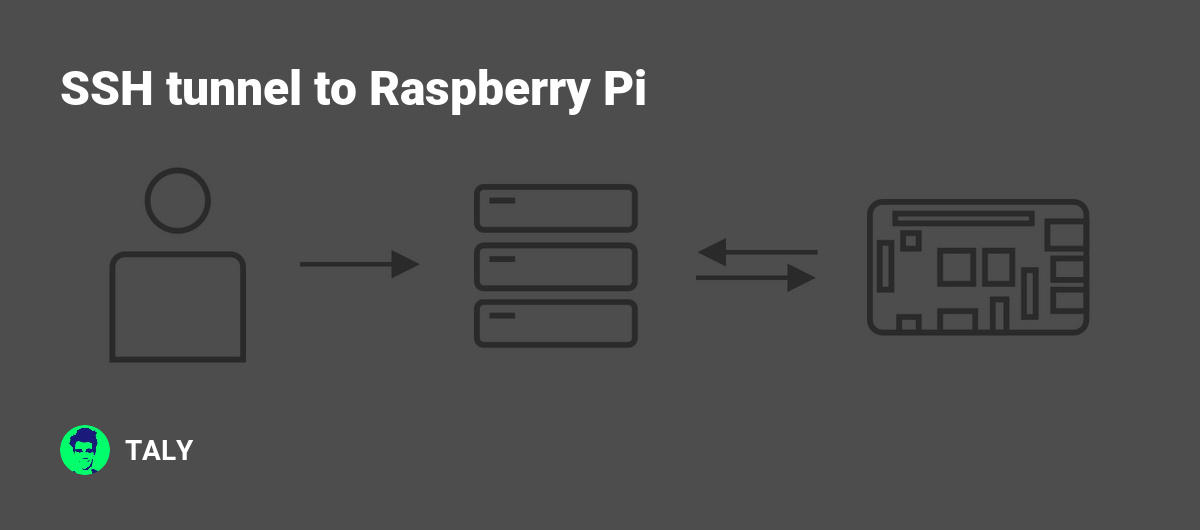
SSH tunnel to Raspberry Pi